- O2 Community
- Discussions, Feedback & off-topic
- Discussions & Feedback
- Security weakness in O2 site
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Security weakness in O2 site
on 18-08-2015 04:49
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
on 18-08-2015 04:49
Something I noticed at the weekend when I tried to log on to O2, and it also happened earlier. I don't have a screenshot, but Firefox failed to connect to O2, bringing up an error page with a message about "incompatible protocol". Strangely, it's not consistent : sometimes I can go through the login process without a hitch.
This must be a result of the change in Firefox 39, when support for SSL 3.0 was dropped. Firefox expects secure connections to use TLS 1.2, although it will allow downgrading to TLS 1.1 or 1.0
The secure elements of the O2 site don't use TLS 1.2; Firefox and Chrome show they're using 1.0 instead. The same applies to other browsers, from IE8 to the new Microsft Edge. In addition, Chrome (click on the green padlock to show the connection information) says, for example, "Your connection to accounts.o2.co.uk is encrypted using an obsolete cipher suite".
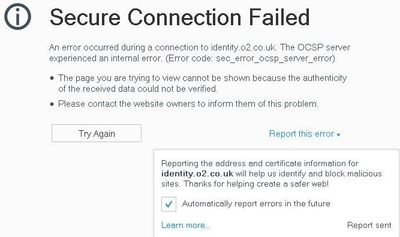
The login problem is caused by a failure to connect to identity.o2.co.uk, and so I ran a Qualys check on it. The results confirmed that this part of the site at least was insecure - see the output from the scan at https://www.ssllabs.com/ssltest/analyze.html?d=identity.o2.co.uk
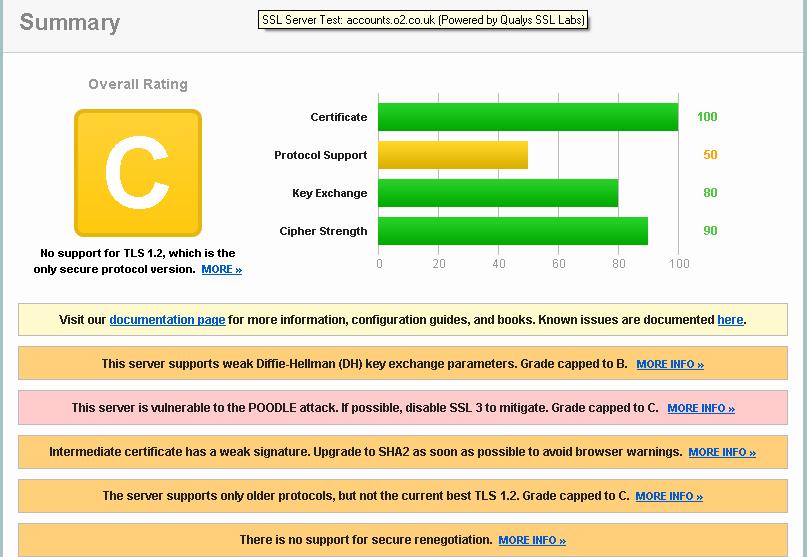
If the same applies to other areas of the O2 site where a secure connection is required that means those areas that deal with account information, purchases and other important matters are potentially using an outdated and hackable protocol. Even TLS 1.0 is considered both weak and vulnerable to hacking.
Someone needs to attend to the website to bring it up to date and fix these security lapses, or sooner or later it could get compromised.
I looked for a way to report this to O2, and found no way to do it. There's nothing on the website to allow you to report a site problem, and unless you have an O2 mobile account the online chat is inaccessible. Even the O2 Facebook page is useless, being filled with PR puffery; anyone trying to ask anything of O2 runs up against what must be one or more lowly Tier-1 techs fending off their enquiries with a set of standard unhelpful responses. O2 is very bad at listening to people, all it seems to want to do is sell some new gizmo or service to you if you have a question or complaint.
In the end I sent a PM about this to Toby (and then discovered he's on holiday) and finally to MarinaP. All I'm concerned with is letting someone know about this who is able to get the attention of the distant suits somewhere upstairs. If this or my PMs do the trick, then good, job done. I've got other stuff I need to be getting on with; it's O2's job to look after its website and stop it being hacked, not mine.
Have a nice day, y'all. I'm clocking off now, it must be nearly rise-and-shine time for normal folks. So head-down-and-sleep time for me 😞
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
on 19-08-2015 10:57
We have feed this back to our online security team and we'll update you whenever we have more info.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
on 18-08-2015 06:51
Hi @Anonymous
We did have problems with the website at the weekend. It didnt matter what you were using. The site was down... As was MyO2. People were also unable to send or receive emails.We had no explanation for that at all
I use Firefox myself and though I didn't get the error message of 'incompatible protocol' it was impossible to get online for over 6 hours.
Since then I have never had a problem logging on.
I honestly can't comment on on the technical side of your statement that O2 is using an outdated and hackable protocol....(I am not that knowledgeable) However you say you have PM'd @Toby and @Anonymous so hopefully you will get a response from them 
Veritas Numquam Perit

- 154828 Posts
- 659 Topics
- 29444 Solutions
on 18-08-2015 08:15
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
on 18-08-2015 08:15
Please select the post that helped you best and mark as the solution. This helps other members in resolving their issues faster. Thank you.
- 98697 Posts
- 617 Topics
- 7253 Solutions
on 18-08-2015 09:17
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
on 18-08-2015 09:17
Both Fiirefox and Chrome report security issues with this site and more of a worry, with My O2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
on 18-08-2015 21:55
I'm not too concerned about the O2 Community pages being delivered over an HTTP connection, although some other sites enforce HTTPS for their own Community. It's the critical areas of the O2 website that use HTTPS that need attention, because the presence of "https" in the address and the green padlock implying a safe and secure connection are both misleading if the protocols and cipher suites involved are 20 years old and have been superseded. Which, apparently, is the case on the O2 servers.
Running a Qualys scan for each area of the O2 site that claims a secure connection (accounts, login, others) should give a clear picture of the strengths and weaknesses of the site as far as secure connectivity goes.
Here is the Qualys summary for accounts.co.uk (report is at https://www.ssllabs.com/ssltest/analyze.html?d=accounts.o2.co.uk). The note about being vulnerable to POODLE attack does not appear on the report for identity.o2.co.uk, nor does the note about Diffie-Hellman key exchange parameters. And yet the server IP address is apparently the same for both. It may be that we need to see a collection of these Qualys reports to get the full picture.
It might also help to make a record of security warnings issued within different browsers. Firefox has both Page Info and Web Console, which will provide complementary sets of information; depending on the security settings within Firefox you may also pick up connectivity warnings and errors such as this one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
on 19-08-2015 10:57
We have feed this back to our online security team and we'll update you whenever we have more info.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
on 19-08-2015 13:49
@Anonymous, thanks for the response and the PM.
The website itself should have a link to enable site problems to be reported, which would have saved a lot of time and effort. O2 is not alone in overlooking the need for technical feedback; even the OU website currently lacks that feature.
I hope O2 improve their IT security, because as things stand there are some serious deficiencies.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
on 19-08-2015 14:23
In my second post (message 5 in the thread) I was wrong when I said ".. the server IP address is apparently the same for both." If you look at the Qualys output you'll see this is not so. O2 has allocated different parts of the visible website to several servers, which is why the Qualys results for accounts.o2.co.uk and identity.o2.co.uk are not identical. This perhaps makes the site more robust - if one server goes down it should not cripple the whole site (unless that server is handling logins) - but it will make improving security across the site more complex, because any changes must be replicated across several servers.
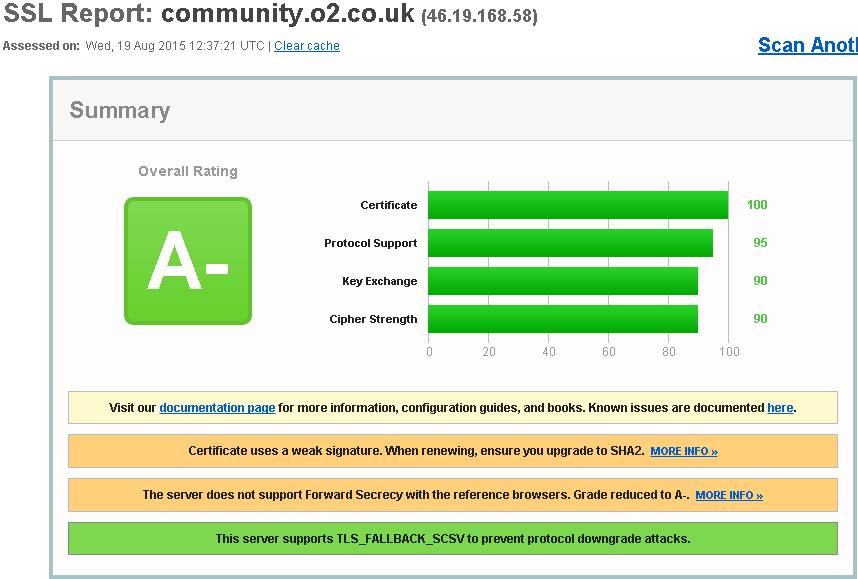
Ironically, the server hosting the O2 Community is better secured than those handling supposedly "secure" functions - note especially the bottom line in this screenshot. It ought to be possible to upgrade the connection to the Community pages to HTTPS, which would bring O2's Community into line with the Communities of some other major companies.
https://www.ssllabs.com/ssltest/analyze.html?d=community.o2.co.uk
There are plenty of other security scans I could run on this site and the the O2 servers, but the basic point has been made and MarinaP has pinged the appropriate people so maybe something will be done to fix the security lapses. I certainly hope so.
- 98697 Posts
- 617 Topics
- 7253 Solutions
on 19-08-2015 15:14
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
on 19-08-2015 15:14
Well all credit to you @Anonymous. All this is way above my pay grade and beyond my comprehension. ![]()
There again, what I don't know about I don't worry about so thanks for giving me some added worry lines on my already well mapped forehead ![]()
- 27018 Posts
- 247 Topics
- 1614 Solutions
on 19-08-2015 23:31
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
on 19-08-2015 23:31
Sky Unlimited Broadband - Windows 10 - Nexus 4 Android 5.1.1
- O2 SENT ME A TEXT ON 07/02/2025 WARNING ME ABOUT UPCOMING 3G AND 2G CHANGES in Discussions & Feedback
- Don't get those 4G backup Home broadband Deals! in Discussions & Feedback
- White Room Quiz Mon 01 Feb 2021 in Off-Topic
- What security features does O2 offer to protect against port-out scams? in Discussions & Feedback
- Phishing text%20from%20o2 in Discussions & Feedback